Threat Modeling? I’ve heard of that before… but: What is “Threat Modeling Workshop” and what is it used for? This blog post is intended to help developers and product managers to understand the concept of the “Threat Modeling Workshop” better. This helps you to check software developments from a security perspective and, if necessary, optimize them in order to achieve a better, and a more secure solution.
The year is 1979.
Some day, maybe Monday, May 13th. A branch. What is to be done today?
Open mail, make phone calls, write down customer data, punch holes, filing, take files to the cupboards on the first floor, room 107. The messenger brings the files to the headquarters on Wednesday, there…
… and so forth. The way it has always been.
The year is 2023.
In software development, we work on automating and thus accelerating business processes. Processes like those in 1979 still exist, but they are no longer the main part of work. Thanks to software, there are far fewer manual administrative tasks in sales, etc. So there are fewer errors – the “human factor” is smaller.
But what about the problems that Software can cause?
In the past, someone would pick out files that people asked for. This person usually also knew whom they could give something to – at least not everything to everyone! Today, software does this work: you start a query, and you see the data. You instruct the program to do certain things and that occurs immediately – not next Wednesday.
But: Does everyone get all the data or just the data they should get? Has anyone considered that the software has to check who is allowed to create/read/change and delete data?
Purpose and goals of Threat Modeling Workshops
This is where we come to the purpose of Threat Modeling Workshops (TMW), as SAP teaches and conducts them itself. (But many other companies also offer TMWs as a methodology. So, the principle is not limited to SAP applications.)
The goal is to always maintain the availability, reliability and confidentiality of the system. These three principles must not be impaired by any software development or application.
New applications must therefore be carefully examined to ensure that they do not compromise these principles.
Software development has to be planned and we do NOT want to use TMW to check whether the application does everything you want it to do functionally, but whether the planning of the application takes all relevant security aspects into account.
Technical architectural models as part of the TMW
This planning, includes software developers presenting what they plan to do or what they have already started. For this purpose, the intentions and processes of the planned application are depicted in the form of technical architectural models as diagrams.
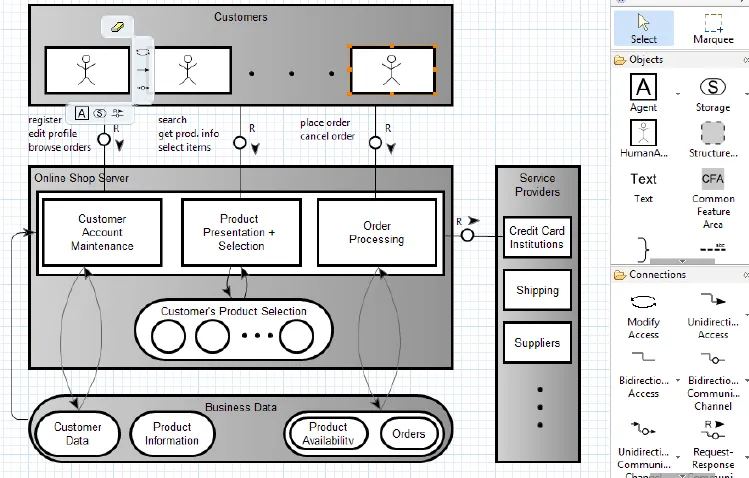
These models use relatively few “graphical vocabularies”. That makes it easy to understand them. Here is an example of an online shop in a block diagram:
Anyone who knows these 15 to 20 “vocabulary words” – some of which can be seen in the right-hand area of the image – is able to read such diagrams. This makes the development transparent. You look at it as a whole – not the individual lines of code. They remain subject to code review.
These technical diagrams are discussed in the Threat Modeling Workshop; weak points, if any, often become apparent here. Such as a missing authorization check.
Examples of results and successes of technical architectural models
After discussing the diagrams, a catalogue of possible security problems from various areas is discussed.
Some examples: The implementation of authorization checks has always been one of the most important topics. But for years, it has always been mandatory to implement protective mechanisms for personal data => keyword “GDPR”. If you don’t pay attention to this, very high fines can be imposed!
An application that deals with and stores personal data is therefore always subject to particularly high security standards. So, these she have to be fulfilled.
In addition, the TMW also checks, among other things, whether data or data queries can be manipulated without authorization via the user interface, so that unauthorized persons can, for example, you can download the entire customer base. This can be done by changing unencrypted HTML strings, e.g. if the query sent in the HTML string is changed or supplemented.
Example: You ask for a specific customer name. This HTML query string shows:
customerName = ‘Neumann’
If you send the query, the data comes to this customer.
Hackers or even someone with “increased curiosity” have it easy here. They would add:
or customerName like %
The query now asks for the data of customers with the name Neumann or any name. This condition is always met – by all customers… and the hacker receives all of the data.
Imagine if this wasn’t a READ command, but a DELETE command! (P.S.: The case, exactly this case, is real.)
It should also be briefly mentioned that the functionality must always be checked to ensure that it does not consume too many resources. Perhaps if a query is too broad and then finds too many sets of results, it can affect the system. The response times are then too long or the system no longer responds, other users are hindered, too much memory is used, etc.
Results within the framework of a TMW
At the end of a TMW there is an OK for the development or list of measures that are carried out and monitored as planning and development changes.
In Short: A “threat modeling workshop” in software development should do its part to protect the three most important characteristics of the system: availability, reliability and confidentiality.
It does this by following a methodology to clearly represent software development in diagrammatic form and allows for the discussion of security standards from different areas.
Questions about Threat Modeling Workshop?
Do you have any questions about TMWs? Simply write to sapentwicklung@inwerken.de. Our development team will contact you! You can find additional services in our portfolio.
Sie haben Fragen zu TMWs? Einfach schreiben an sapentwicklung@inwerken.de. Unser Entwicklungs-Team meldet sich bei Ihnen! Leistungen darüber hinaus finden Sie in unserem Portfolio.